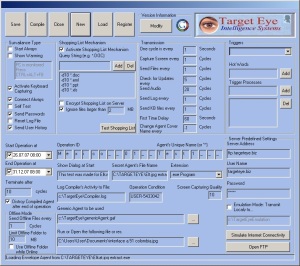
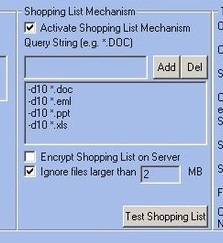
This post contains part of the original Business Plan created in May 2000.
Target Eye Limited was registered in Israel, Delaware and in the UK. It was founded in 2000 as a startup focusing in remote PC monitoring for surveillance purposes.

Executive Summary
Target Eye is a start-up company whose mission is to develop integrated software solutions for real-time monitoring and control of remote PCs, which are based on the company’s patent pending technologies (60/204,084 and 60/203,832).
The company is registered in Delaware and its R&D division is located in Tel-Aviv, Israel.
The company is owned and managed by Mr. Michael Haephrati, a well-experienced business manager and expert in the fields of computer security, intelligence, information systems and software development.
The company’s major product, Target Eye, is a software product that can continuously track, record, playback, analyze and report any activity performed on one or multiple remote computers, in a way which is undetectable by their users.
The software relies on a stream of rapidly captured, compressed full-screen images and continuous keystroke capturing to provide a comprehensive and accurate account of user activities, including local activities which do not generate any network traffic. In this way, the software can track and record activities, which are undetectable by systems relying on network traffic analysis.
A Secret Agent module running on the monitored PCs uses a rule base to send alerts to the monitoring location(s) or perform pre-defined local operations. Monitoring can be performed from multiple locations.
Major markets include the Law Enforcement and Intelligence markets, the E-Support market, the E-Learning market, and the corporate market. We see a growth potential for these rapidly expanding markets and estimate a revenue projection of over $90M in the next 3 years.
Additional Information:
Target Eye markets its technology and products using worldwide distributors.
We will also approach companies selling to the same target markets, which already have the infrastructure for worldwide distribution. These include manufacturers and distributors of security products, E-Learning products, E-Support products, etc.
The Market
Target Eye sees the following markets as potential markets for its line of products:
• The Law Enforcement market
• The corporate and outsourcing market
• The E-Learning market
• The E-Support market
The Law Enforcement Market
In today’s age of terrorism and cyber crimes, when fraud is becoming the biggest moneymaking opportunity on the Internet, more and more illegal activities are being preformed with the use of computers. In many cases, the criminals are better equipped than the victims.
While these activities occur, Law Enforcement bureaus are urging for a high technology cyber weapon that will allow a cyber war against cyber crimes.
Security, personal protection, national protection, confidential business information theft and industrial espionage represent a $20 billion market (according to COMSEC). This market is expecting a rapid growth. Industry analysts are predicting a growth of up to $40 billion during the next five years.
Government leaders as well as Law Enforcement professionals and national security bureaus have a lot to worry about, as security concerns are becoming a major issue not only for banks and corporations, but also for schools, universities, municipalities and small businesses.
The quickly escalating situation is prompting a new legislation spirit in the US and other countries around the world, intended to allow Law Enforcement bodies to catch cyber criminals using high technology tools such as computer surveillance systems. On April 27th, 2000, the European Council released a draft version of a convention paper on cyber crime, intended to coordinate national legislation efforts for the prevention and treatment of cyber threats.
These factors open some new and exciting business opportunities for participating in what is expected to be a $40 billion market in the next five years.
Target Eye is a uniquely suitable offering in this market, due to its use of a Secret Agent module that allows a computer to be remotely monitored in a covert way, without the user being able to detect he is being watched over. Also, the HotWord alerts mechanism draws the attention of the controller to any one of a number of monitored users upon encountering “sensitive” information or suspected activities.
The Corporate and Outsourcing Market
The corporate market consists of companies wishing to deploy tools for analysis and enhancement of employee productivity, remote employee management, and in-house investigation and surveillance.
More than 78% of large U.S. firms record and review employees' communications and activities on the job, twice as many as reported in 1997, according to an April survey by the American Management Association (AMA). The measures introduced in the House and Senate would not force employers to change their surveillance habits and would not require them to notify employees each time they check on them. The AMA questionnaire listed these forms of electronic monitoring and surveillance:
At the moment, monitoring for most companies means tracking e-mail and Net use, but there is an increasing interest in other uses of monitoring such as fraud detection, employee productivity analysis and enhancement, and remote employee management tool.
Outsourcing is another promising market for Target Eye. Today, more and more companies outsource a portion of their development or support activities to offshore or otherwise remotely located organizations and subsidiaries.
The Target Eye technology enables quick and effective online collaboration between local and remote employees, providing a great tool for streamlining outsourcing types of projects. Target Eye wishes to capitalize on expanding needs in order to provide a wide range solution for this market..
Some of the similar products attempt to perform remote real time monitoring of live screen images, and in doing so, use significant computation and communication resources. These systems lack the ability to capture ‘live’ screen images and transmit them to a distant network without overloading the network.
Two examples of such systems, called professional and Boss Everywhere, operate on a central PC server and run several applications simultaneously for a number of users which use remote Windows PC's as terminals. These system offer no real tracking / monitoring functions. In MS Windows based servers, such monitoring systems rely on Windows kernel changes at the server level.
Another type of remote monitoring products, such as PC Anwhere, remotely take control of a given PC. This is done visibly and requires the consent of the remote user. The goal in these systems is remote access rather than remote monitoring. A further type of monitoring systems capture the address of the displayed item and retrieve it from its original source, rather than from the monitored station over which it is browsed as a screen image.
Another system called Platinum automatically collects system events and stores them in a central database. This system is geared towards system administrators.
Using existing methods such as transforming a bitmap image of the active window and yet keeping a reasonable refresh rate, which is expected from a monitoring system, requires 500KB-1MB of storage space and communications bandwidth per image, which makes it not feasible in this application.
Target Eye contains methods and systems for monitoring activity in general, and methods and systems for monitoring personal computer activity, in particular.
Target Eye uses a hierarchical Client-Server / Server-Client structure, which overcomes the disadvantages of other products, currently marketed. Figure 1 depicts a schematic illustration of a system according to a preferred embodiment model of Target Eye.
Our major product, TargetEye, is a software product that can continuously track, record, playback, analyze and report any activity performed on one or multiple remote PCs, in a way which is undetectable by their users.
The software relies on a stream of rapidly captured, compressed full-screen images and continuous keystroke and mouse event capturing to provide a comprehensive and accurate account of user activities, including local activities which do not generate any network traffic. In this way, the software can track and record activities, which are undetectable by systems relying on network traffic analysis.
A Secret Agent module running on the monitored PCs uses a rule base to send alerts to the monitoring location(s) or perform pre-defined local operations. Monitoring can be performed from multiple locations.
Major Target Eye Features:
• Continuous real-time display of a remote PC’s screen image and keystrokes, using a relatively small stream; our scalable technology ensures quality of transmission even over a 33.6K dial-up connection.
• Simultaneous monitoring of several remote PCs.
• A comprehensive set of OS-derived data for the monitored PCs, such as task list, active task, idle time, open data files and current URL are also collected and displayed.
• Rapidly updating full-screen images enable tracking short-term or transient activities, such as creating a Word document and subsequently deleting it. The activity will be captured even though it will not change the local machine state nor generate any network traffic.
• VCR mode records screen images and keystrokes from a large number of monitored PC’s for later replay. This addresses the limitation of a human viewer not being able to monitor a large number of PCs in real time, as well as allowing for unattended operation.
• A Secret Agent module running on the monitored PCs uses a rule base consisting of pre-defined keystroke sequences (HotWords™) and OS data rules to send real-time alerts or perform local operations upon encountering “sensitive” activities or data. Compound rules can be specified, such as:
IF TASK = “outlook express” AND HOTWORD = “James Bond” DO send_alert [1].
If the rule becomes true, an alert is immediately sent to the controller, with a designation of the suspect station.
Compound rules are an effective tool for tracking suspected activities in real-time and performing any required interventions. Combined with support for string variables and wildcard specification, they can be effectively used for such tasks as detecting who is drawing money from a certain bank account, what email messages were sent to a competing company, and which employee is inappropriately using four-letter words in his email correspondence.
• The controlling program can update the rule base used by the Secret Agent over the connection. HotWords™ and OS data rules can be added on the fly, so that the system can be kept fully up-to-date on sensitive information for which real-time alerts are crucial – without requiring re-installation or further access to the monitored computers.
• The Controller program can take full control over the monitored computer. It can, for example, display a message on the monitored computer and force it to turn off.
• Using the Co-Work feature, the controller and the user of a remote PC can simultaneously operate the remote PC, facilitating such applications as e-learning, employee training, and remote maintenance.
• A Reporting Module generates meaningful reports that can include such data as complete daily log of tasks for employee, total time in task, idle time in task, total time idle, URLs visited, and other information, which may be used to analyze and improve employee productivity.
• TargetEye does not depend on network traffic analysis for its monitoring and tracking abilities, as do most systems on the market; instead, it relies on actual screen images, keystrokes, and OS information. This allows it, for example, to view locally encrypted e-mail, something programs using network traffic analyzer fail to do.
System Architecture
Target Eye overcomes the disadvantages of other products by providing a novel architecture and a method for implementing it, which is based on templates.
Figure 2 shows a schematic illustration of a network environment and a monitoring system, constructed and operative in accordance with a preferred embodiment model of Target Eye.
Target Eye Secret Agent 1 is an invisible component that can be discretely installed on the PC being monitored. This component can capture graphical and textual data, perform various operations upon request sent from the controller, and configure itself to activate automatically whenever the computer is turned on.
Target Eye Agent Monitoring Server 2 handles data transfer between one or more Secret Agents to the controller via a Remote HTTP Server 3, or directly.
Remote HTTP Server 3 represents, receives and transfers data between the agent monitoring server 2 and the Controller Server 4.
Target Eye Controller Server 4 is preferably implemented in software, collects information received from the Secret Agent 1 and delivers it, regularly or upon request to the controller client 5.
Legal Protection:
The Target Eye technology is protected by U.S. pending patents No. 60/204,084 and 60/203,832.
The patents were filed between April 2000 and July 2000, by Michael Haephrati.
Michael Haephrati
Michael has 18 years of experience in the areas of managing software and system operations, including extensive experience managing through entire life–cycle of several start-ups and software products including:
• THIS )Targeted Human Intelligent Scoring( ©1998-2000. Served as VP Business Development and General Manager.
THIS is an integrated financial scoring system, which uses mathematical and logical models developed in recent years. The software generates quantitative indices (Scores) reflecting a customer’s financial soundness, reliability, and the level of significance at which the customer can be graded. .It can utilize a variety of DBs, whether existing or furnished by its user The object of THIS is to reduce the number of loans and mortgages given to people, when there is a high expectation that repayment obligations will not be met, without rejecting applications of potentially reliable customers who, on the surface, do not appear suitable, or who might be offended by a multitude of questions that invade their privacy and whose custom we do not wish to lose.
• People ©1999, Served as VP Business Development.
People is a “spell checker” mechanism for resolving wrong addresses. Working in batch or manual modes, the software uses an address database, geographically identifies each address, and converts it into a unique identifier (UID), providing the appropriate co-ordinates along with any other known data about the address.
• Rashumon ©1989-1995. Served as the CEO.
Rashumon is a multilingual word processor developed under AmigaDOS, MS-DOS and Mac System 7. Rashumon was the first word processor to offer features such as text-to-speech output of selected parts of the document, multiple selections, Postscript level 2 support as well as features which are common today in most word processors (WYSIWYG support, graphic support, etc.)
Several patents have been issued to Michael, who has published more than 50 technical articles and columns in magazines such as 32 Bit and People and Computers. Mr. Haephrati was a consultant and wrote the material for a computer section in a TV program produced by the Israeli Instructional TV, and taught several courses in Computer Programming, Music and Computers and Computers and Art.
Michael is a professional software developer who specializes in Visual C++ MFC as well as Visual Basic, Delphi programming for Windows, DOS and Mac OS platforms.
Michael also worked with Apple, Cupertino, and started his career with Tadiran Computers in 1986, providing technical support for the Amiga line of personal computers.
Michael is a member of several closed organizations, among them are:
• The International Association of Financial Crimes Investigators (IAFCI)
• The International Association of Competitive Intelligence Professionals
• The Israeli Senior Board of Competitive Intelligence
• The American Society for Industrial Security (ASIS)
• International Association For Counter-terrorism & Security Professionals (IACSP)