How Target Eye Monitoring System can be used for a complete solution for Law Enforcement Agencies
Target Eye Limited is a software company registered in the UK, which specializes in security related applications and projects. It was established on 2000 and has been developing a unique surveillance over PC technology since.
Based on the special requirements of Law Enforcement agencies, it is important to provide them with a complete solution which will cover all of their needs. The opportunity to base such solution on a working platform, i.e. the Target Eye Monitoring System, and yet, amend it and add to it any missing elements, seems to be the best solution for their need.
When you take into consideration 5 years of development, which has led to a mature product, along with the detailed solution we are offering to every aspect of their needs, it leads to the conclusion that our system plus our knowledge can bring you’re your client to the best solution in a relatively short time.
What makes Target Eye Monitoring System special
● It can hide itself and stay undetectable
● It can activate itself and completely remove itself at the end of it's life cycle.
● It can Record keystrokes, using a unique multilingual engine, that is a one of it's kind, as it does not require any DLLs. It uses a unique technique which is non detectable, as it doesn't use any “Hooks”, as other key loggers do.
● It has a unique Screen Capturing capabilities, which enables you to control the quality of the images.
● It works both on-line and off-line
● Collects information about all activity, off line and on line, including searches, Auto Complete fields within programs such as Internet Explorer, etc.,
● Provides full access to encrypted email accounts passwords, Windows XP Protected Storage passwords, etc.
● Can get files that are kept in external media, even if they are accessed only when the monitored computer is off line.
● Can get deleted files from the Recycle Bin.
● Using a unique Resource Manipulator, build in as part of the Compiler, the Secret Agent “Creation Date”, “Company”, “Legal Trademarks”, icon can all be determined using the Compiler.
● Secret Agent can disable Windows XP firewall, while sending material to the Internet.
● The Shopping List mechanism is a unique method for dual way communication with the Secret Agent, enabling making specific queries and requests, while being updated as for their outcomes, in real time.
● A trigger based rule system that can be used to perform certain actions as a result of certain circumstances. For example: temporarily stopping any Internet communication when a certain Process is running.
● All files and folders created while monitoring the Target PC, are hidden, even when the “Show Hidden Files” option is set.
General considerations.
Unlike other interception methods, which are used by Law Enforcement Agencies over the years, such as telephone surveillance, the field of computer forensics requires a unique solution which will enable surveillance on any activity which take place using a computer, in one hand, and in the other hand, will be up to date (and will remain as such), taking into consideration the rapid change in that field.
In today's world, next to any activity, is related in one way or another, to computers. Memos, agreements, thoughts, plans, correspondences, documents, are all prepared, read, edited and produced using a home PC.
The new era of global terrorism, which especially came to the attention during the events that shocked the world on 9/11, and also domestically, the rapid growth in the need to fight against, organized crime, both combined with the almost definite weight computers have within any (criminal) activity, generate an urgent need to address these risks and to provide Law Enforcement Agencies, a Computer Surveillance, Monitoring and Information Gathering tool which will be the 21st century equivalent of the old telephone surveillance methods.
Such solution must assure that ANY information which is stored or produced (even temporarily) in a computer, regardless of the activity, software, purpose, connectivity that computer is using in any given moment, will be captured, in a way that will be producible to court when time comes.
We have learned from requirements given by agencies that a unique system such as Target Eye Monitoring System, after being customized and additional turn-key development, can be the right answer to their needs.
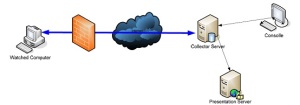
General Architecture
The system consists of 4 elements:
- The TargetWatch Agent (which is equivalent to the Secret Agent in the Target Eye Monitoring System).
- The Data Collector / Consolidator (which is not part of the Target Eye Monitoring System architecture).
The Target Eye architecture is based on a slight different concept:
- The core base of the system is the Secret Agent. The Secret Agent runs covertly regardless of the current connectivity state. Every bit and piece of information can be captured and to be either stored in the Vault, which is a hidden storage place used by the Secret Agent, or to be sent to the Server. While information is sent to the Server in real time, the Secret Agent also send old information which was previously kept in the Vault.
- A Passive Server. We believe that there is no need and no use of a Server side software. We have designed an architecture which is based on a Passive Server (such as FTP) which receive the encrypted data from the Secret Agent. Another software component, which is optional, can then download the data and decrypt it. Such component could be a full Controller software, or a simple FTP client but also the basic Target Eye Decryption software which can be used to decrypt files which were already downloaded using the Windows regular Explorer. We believe that such simplicity allows the end user to address a greater number of scenarios. Such flexibility allows the Operator to change Agent's broadcast to a different address on the fly.
- The Controller software. Back on 2000, we have developed a graphical MDI designed Controller software. That project was never commercially released, but it seems that such software can be handy for this project.
- The Encryption tool. We have developed a tool that can identify encrypted Target Eye files and decrypt them back to their original file.
- The Licensing module. We have developed a tool that is used to control the license to create Secret Agents. A license can encapsulate one or more of the following characteristics:
- Number of Agents left to compile
- Overall time left for all agents to run (total)
- Overall operations left
- Hardware Specifications.
The solution required by most Law Enforcement agencies, would usually be implemented over an average computer such as a workstation or a laptop running Windows XP. A special solution for Vista and Windows 7 is available as well.
- Software specifications.
The software we provide is compatible with most if not all Windows operating systems. However, the Secret Agent software, does not require any installation (no Setup.exe is needed), will not reveal itself even in cases of being non compatible with the operating system (for example: no error messages or dialog boxes will ever appear).
- Installation and project management.
Our projects are turn-key projects, and at a certain stage, one of our experts arrive to the customer's site in order to take part of the installation of the software.
Project Managers is usually assigned to the project from both sides (Agency / TargetEye) and should communicate one between the other, regarding any milestone, open issues etc. Such project should last 6 months, but an operational environment should be installed at the client's site within 3 months, and be used until the completion of the project, when an operational environment will replace it.
Configuration Management
There is a list of preset settings which will be available to the client upon installation. These include:
- Server settings
- Unique Identification Number
- Default Secret Agent settings (including pre made templates).
Performance management and QA
We usually provide a QA expert which will accompany the entire life cycle of each project.
At first, the QA person compose a Test Plan which will later be used to run a serious of tests to approve new releases each time. Simultaneously, the QA expert will try to find flaws in the system and suggest improvements accordingly. When it comes to performance, the following points must be considered:
- StabilityFor obvious reasons, the Secret Agent software must not crash, especially with a Windows failure dialog being displayed.
- WorkloadsThe system workload must not increase in such way that will be noticeable to the monitored computer's user.
- Fault management.Define the faults for which you expect the vendor to assume responsibility. Defining boundaries of responsibility is critical, otherwise you and your vendor will be finger-pointing for the life of the contract. A vendor's response to this section will tell you how it manages networks, the vendor's network management infrastructure and the number and experience of network management personnel.
Security management.
We have designed a model which can be implemented in order to provide security management for all operations of the system.
There are four basic entities in our model:
- The Operator, which is the agency or the department within the agency who operate the Target Eye system.
- An Operation, which is the activity which is initiated and conducted by an Operator, and includes transplanting and using a Secret Agent on a Target.
- A Target is a person or a location where we expect to find the information we are looking for. A Target could be a certain Executive Lounge in a Hotel, or an Executive who works for a certain organization.
- A Secret Agent, which is the actual software installed in a sTarget PC.
For further information write to: sales@targeteye.biz
Articles and source code of previous versions

No comments:
Post a Comment