Further reading:
The following analysis was made on Target Eye (2004) by "Zak", a former IDF Cyber Crime Unit Chief (at least he claims to be...).
A surveillance software must not be revealed and if revealed, there is a need to change it rapidly so the next version will be 100% stealth. Being revealed marks the end (or at least the end of the revealed version). See for example a similar product.
- The Target Eye Cover Story mechanism
- The Target Eye Shopping List mechanism
- The Target Eye Auto Update mechanism
- The Target Eye File Hiding mechanism
- The Target Eye Keyboard Capturing mechanism
- The Target Eye Screen Capturing mechanism
The following analysis was made on Target Eye (2004) by "Zak", a former IDF Cyber Crime Unit Chief (at least he claims to be...).
A surveillance software must not be revealed and if revealed, there is a need to change it rapidly so the next version will be 100% stealth. Being revealed marks the end (or at least the end of the revealed version). See for example a similar product.
Since the 2004 version, the 2005 was launched right after and unlike the 2004 version, was not blocked by Anti Viruses and Firewalls.
Some parts of the report is incorrect and some were correct to that time (mostly the 2004 version) and were fixed as part of the 2007 version.
Needless to say that Target Eye and similar products are sold (can must be sold) to governments only, especially to law enforcement agencies and other cyber crime task forces.
Deployment of payload
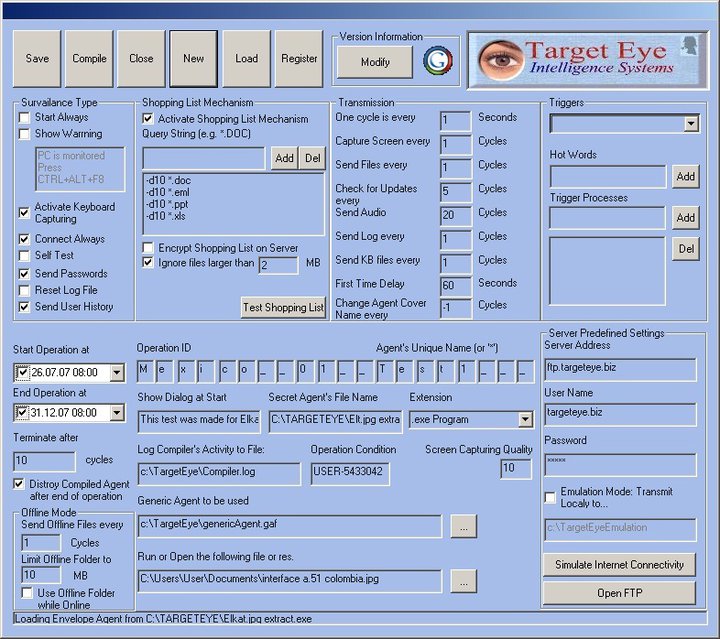
The Target Eye Secret Agent was deployed via a "payload" we refer to as our "Cover Story", or "Customized Agent". The purpose of the Customized Agent is to make the Target Eye software look like something else, convincing the suspects to open it.
That can be a disguise of a password protected document. You can read more about this mechanism Target Eye Cover Story. The 2004 version was marked as "IL-trojan" (in other words, it was "burned".
That can be a disguise of a password protected document. You can read more about this mechanism Target Eye Cover Story. The 2004 version was marked as "IL-trojan" (in other words, it was "burned".
The "researcher" probably preferred to save the payload as a .txt file for his own protection. However in order to make such payload run, it must be either a program (which can be .exe, .bat. com, etc.) or use an exploit which can embed itself in a data file such as .pdf.
Target Eye (2004) did not use any exploits, but had the mechanism to set the executable's icon, making it look like anything else. For example, making it look like a "Word" document:
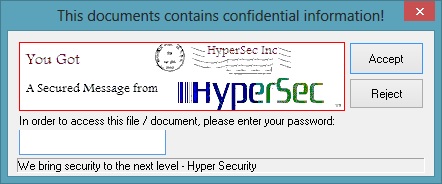
As the suspect clicks on the file – the following screen appears. The original report claims that regardless of the password entered, the Target Eye Secret Agent is installed. That is not correct. In fact, as opposed to a virus whose goal is to spread all over, a surveillance software targets a specific computer and intend to install itself only there. So the password was another mechanism, along with IP address and default email account which were used in this version (and are still used in current versions) to identify the target of the suspect being investigated.
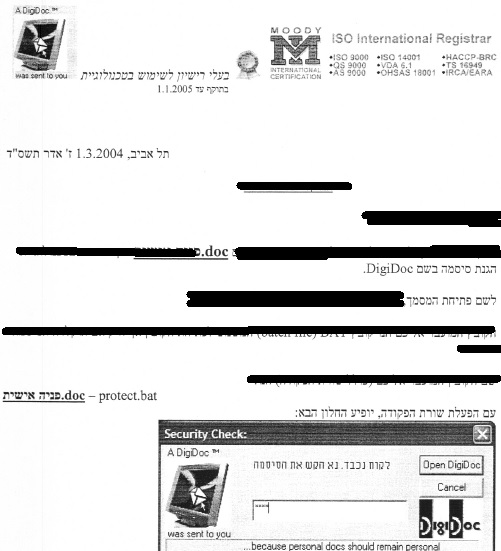
In the above photo, taken from the original report, our "Ziplip" Cover Story. Another version of it is the "Digidoc" one:
As part of our series of articles about Target Eye, I have released a real letter sent in order to convince a target to open the Target Eye payload that followed.
Which Anti-Viruses / Firewalls identified Target Eye (2004)
Which Anti-Viruses / Firewalls identified Target Eye (2004)
Zak continues and claim he run the Target Eye Agent through Virus Total to see who can spot it.
Antivirus Version Update Result
AntiVir 6.30.0.15 06.03.2005 TR/Spy.Hotworld.A
AVG 718 06.04.2005 PSW.Hotworld.I
Avira 6.30.0.15 06.03.2005 TR/Spy.Hotworld.A
BitDefender 7.0 06.04.2005 no virus found
ClamAV devel-20050501 06.05.2005 no virus found
DrWeb 4.32b 06.03.2005 Trojan.PWS.Pinka
eTrust-Iris 7.1.194.0 06.04.2005 Win32/Hotworld.A!Trojan
eTrust-Vet 11.9.1.0 06.03.2005 Win32.Hotworld.A
Fortinet 2.27.0.0 06.04.2005 W32/Hotworld.A-spy
Ikarus 2.32 06.03.2005 no virus found
Kaspersky 4.0.2.24 06.05.2005 Trojan-Spy.Win32.Hotworld.a
McAfee 4506 06.03.2005 PWS-Hotworld
NOD32v2 1.1127 06.04.2005 probably unknown NewHeur_PE virus
Norman 5.70.10 06.04.2005 no virus found
Panda 8.02.00 06.03.2005 Trj/Rona.A
Sybari 7.5.1314 06.05.2005 PWS-Hotworld
Symantec 8.0 06.04.2005 Trojan.Hotword.B
TheHacker 5.8-3.0 06.04.2005 no virus found
VBA32 3.10.3 06.03.2005 Trojan-Spy.Win32.Hotworld.a
Zak tells his workers in the lab to take care…
Hi all
The majority of the vendors have updated their signatures after it was
published, for example Symantec has classified it as 0-49 infections
virus.
You can run it freely, it will created some screenshots, open https, and
store your http links
Just don't forget to delete " svchost.exe" (with space) file in the
system32 folder
Z.
What happens after Target Eye is installed on the suspect's system
The image above is taken from Zak's original report.
Following is a description of Target Eye's log file which contains the following indications:
Following is a description of Target Eye's log file which contains the following indications:
- Can Install 1
1 - means that Target Eye was successfully installed on suspect's machine.
- Can Receive 0
0 - means that Target Eye failed to receive data from the server, as the communication should be dual way.
- Can Send 0
- Can Send 0
0 - means that Target Eye failed to send data ("I am alive" data) to the server
- Can write to registry 1
- Can write to registry 1
1 - means that Target Eye has successfully wrote to the Registry, which was needed to make Target Eye auto run.
- Cycle 0
- Cycle 0
The Cycle is the base "heatbeat" of the software, so anything that happens, such as any monitoring activity, takes place every such and such "cycles".
Following are real data from the log file which outline various pieces of information related to the server, online time, offline time, etc.
Files Sent 0 Last FTP update 01.01.1970 02:00 Last Offline 06.06.2005 11:36 Last Online 01.01.1970 02:00
Following are real data from the log file which outline various pieces of information related to the server, online time, offline time, etc.
Files Sent 0 Last FTP update 01.01.1970 02:00 Last Offline 06.06.2005 11:36 Last Online 01.01.1970 02:00
Last query 01.01.1970 02:00 Last settings update 06.06.2005 11:35
Logs sent 0 Screens sent 0 Start Time 06.06.2005 11:35
Work path D:\WINDOWS\system32
Target Eye is active in Zak's PC and gives its first action report:
[0] [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe SA TEST OK "D:\WINDOWS\system32\ svchost.exe" ccRegVfy
Means that the Target Eye Agent was installed in the default System32 folder following its start from Zak's desktop, so the location and name of the Target Eye Agent is different than the original payload's name and location where it was started.
The following part of Zak's report seems to be a demonstration of the Target Eye's Shopping List Mechanism.
[0] [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe ******************************************************************************
[0] [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe 0 (Ver: *** [0.92 AUG] ***Aug 16 2004 13:20:47) st@ 06.06.2005 11:35 fr D:\Documents and Settings\Zak\Desktop\IL-trojan.exe
[0] [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe ******************************************************************************
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe BOP
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe RN FL to: __OPO1__29053044-files.txt
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe EXD=T
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Q '*.doc;*.eml;'
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe IN QE'*.doc;*.eml;'
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe [Q] *.doc
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe [Q] *.eml
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe [Q] *.doc
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe [Q] *.eml
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Error Log StartAlways Error unregistering old self (2) 0
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Error Log StartAlways Error unregistering old self (2) 0
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Ki IL-trojan.exe (IL-trojan.exe)
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Found IL-trojan.exe - 3816
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Found Self IL-trojan.exe - 3816
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Ki explorer6.exe (explorer6.exe)
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe :)
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe P = (null)
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe V=Ver: *** [0.92 AUG] ***Aug 16 2004 13:20:47
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe RBU = T
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe ? 'D:\Documents and Settings\Zak\Desktop\IL-trojan.exe' / 'D:\WINDOWS\system32\ svchost.exe'
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Ki Windows Objects.exe (Windows Objects)
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Ki svchost.exe ( svchost.exe)
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe C D:\Documents and Settings\Zak\Desktop\IL-trojan.exe -> D:\WINDOWS\system32\ svchost.exe. OK
[0] 29053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe Error Log Open by object Wrong password was keyed in 0
[0] C729053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe BOP
[0] C729053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe RN FL to: __OPO1__C729053044-files.txt
[0] C729053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe ND EX
[0] C729053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe EX D:\WINDOWS\system32\ svchost.exe ccRegVfy
[0] C729053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe T
[0] C729053044 [06.06.2005 09:35]: D:\Documents and Settings\Zak\Desktop\IL-trojan.exe HD VR RN I QU
[0] [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe SA TEST OK "D:\WINDOWS\system32\ svchost.exe" ccRegVfy
[0] [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe ******************************************************************************
[0] [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe 0 (Ver: *** [0.92 AUG] ***Aug 16 2004 13:20:47) st@ 06.06.2005 11:35 fr D:\WINDOWS\system32\ svchost.exe
[0] [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe ******************************************************************************
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe BOP
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe RN FL to: __OPO1__C729053044-files.txt
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Q '*.doc;*.eml;'
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe IN QE'*.doc;*.eml;'
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe [Q] *.doc
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe [Q] *.eml
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe [Q] *.doc
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe [Q] *.eml
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe 10.171.3.98
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Error Log StartAlways Error unregistering old self (2) 0
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Error Log StartAlways Error unregistering old self (2) 0
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Found svchost.exe - 2412
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Ki explorer6.exe (explorer6.exe)
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe :)
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe P = ccRegVfy
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe V=Ver: *** [0.92 AUG] ***Aug 16 2004 13:20:47
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe ? FT
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe F
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe RFHP = T
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe NEW DAY? Today=06.06.2005 Last Scan = 03.06.2005
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe DAILY 06.06.2005
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe ? OFL FL
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe OFL FL LST...
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe FN: 0 FL (0 KB)
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Error: Could not open counter registry key
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe DQ -d1 *.bak;-d1 *.doc;-d1 *.xls;
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Open Query [Q] -d1 *.bak
[0] C729053044 [06.06.2005 09:35]: D:\WINDOWS\system32\ svchost.exe Days=1
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe 'Query: *.bak in all drives (C-Z) for the last 1 days
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe FN: 0 FL (0 KB)
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Open Query [Q] -d1 *.doc
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Days=1
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe 'Query: *.doc in all drives (C-Z) for the last 1 days
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe FN: 1 FL (0 KB)
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe DQ -> :) -> 4
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe TE_S ry: *.doc in all drives (C-Z) for the last 1 days
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe IsCon?
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe FT CN !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe TE_S d:\Documents and Settings\Zak\Local Settings\Temp\~WRD0001.doc
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe IsCon?
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe FT CN !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Open Query [Q] -d1 *.xls
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Days=1
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe 'Query: *.xls in all drives (C-Z) for the last 1 days
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe FN: 0 FL (0 KB)
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe TE_S D:\WINDOWS\system32\CFXP.DRV
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe IsCon?
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe FT CN !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe IsCon?
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Send Passwords
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe IsCon?
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Try to send keyboard file
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Going over -1 files found
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe ErL 0
113520 StartAlways Error unregistering old self (2) 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe ErL 1
113520 StartAlways Error unregistering old self (2) 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Connection Test...
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe SA TEST OK "D:\WINDOWS\system32\ svchost.exe" ccRegVfy
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Test 1 OK
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Reset ftp settings
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe c: fur1xfxnm}nl€n<qy‹ u: tbtjiyjh|j8mu‡ p: cj{]PsL
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe Start: error The server name or address could not be resolved
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe IsCon?
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe TE_S TE_FILELOG
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe IsCon?
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe FT CN !
[0] C729053044 [06.06.2005 09:36]: D:\WINDOWS\system32\ svchost.exe End of DAILY 06.06.2005
[0] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe KL Pro List DigiDocSystem.exe;explorer6.exe;Windows Autoupdate.exe;
[0] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki DigiDocSystem.exe (DigiDocSystem.e)
[0] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki explorer6.exe (explorer6.exe)
[0] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki Windows Autoupdate.exe (Windows Autoupd)
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe 06.06.2005 11:37 Solitaire
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Look4ALike
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe IsCon?
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe !
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe SC (OL) D:\WINDOWS\system32\OLECLISystemUpdate_06.06.2005 11.37.15.DLX
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe KL Pro List DigiDocSystem.exe;explorer6.exe;Windows Autoupdate.exe;
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki DigiDocSystem.exe (DigiDocSystem.e)
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki explorer6.exe (explorer6.exe)
[1] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki Windows Autoupdate.exe (Windows Autoupd)
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe 06.06.2005 11:37 D:\WINDOWS\system32\cmd.exe
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Look4ALike
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe IsCon?
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe !
[2] C729053044 [06.06.2005 09:37]: D:\WINDOWS\system32\ svchost.exe SC (OL) D:\WINDOWS\system32\OLECLISystemUpdate_06.06.2005 11.37.45.DLX
[2] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe KL Pro List DigiDocSystem.exe;explorer6.exe;Windows Autoupdate.exe;
[2] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki DigiDocSystem.exe (DigiDocSystem.e)
[2] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki explorer6.exe (explorer6.exe)
[2] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki Windows Autoupdate.exe (Windows Autoupd)
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe 06.06.2005 11:38 Windows Task Manager
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Look4ALike
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe IsCon?
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe !
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe SC (OL) D:\WINDOWS\system32\OLECLISystemUpdate_06.06.2005 11.38.15.DLX
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe KL Pro List DigiDocSystem.exe;explorer6.exe;Windows Autoupdate.exe;
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki DigiDocSystem.exe (DigiDocSystem.e)
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki explorer6.exe (explorer6.exe)
[3] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki Windows Autoupdate.exe (Windows Autoupd)
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe 06.06.2005 11:38 untitled - Paint
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Look4ALike
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe IsCon?
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe !
[4] C729053044 [06.06.2005 09:38]: D:\WINDOWS\system32\ svchost.exe SC (OL) D:\WINDOWS\system32\OLECLISystemUpdate_06.06.2005 11.38.45.DLX
[4] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe KL Pro List DigiDocSystem.exe;explorer6.exe;Windows Autoupdate.exe;
[4] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Ki DigiDocSystem.exe (DigiDocSystem.e)
[4] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Ki explorer6.exe (explorer6.exe)
[4] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Ki Windows Autoupdate.exe (Windows Autoupd)
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe 06.06.2005 11:39 Save As
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Look4ALike
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Ki svchost.exe ( svchost.exe)
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe Found Self svchost.exe - 2412
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe IsCon?
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe InternetgetConnectedState = 0
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe !
[5] C729053044 [06.06.2005 09:39]: D:\WINDOWS\system32\ svchost.exe SC (OL) D:\WINDOWS\system32\OLECLISystemUpdate_06.06.2005 11.39.15.DLX
Target Eye reports browsing history
WWW: URL=http://www.google.com/search?hl=en&q=secureol+gartner Visited = 05.06.05 09:08
WWW: URL=http://www.omnivee.com Visited = 05.06.05 11:22
WWW: URL=http://www.cinagen.com/extra7.shtml Visited = 05.06.05 21:05
WWW: URL=http://www.miw.co.il Visited = 05.06.05 09:57
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095089,00.html Visited = 05.06.05 18:18
WWW: URL=http://images.google.com/images?q=wanna+be&hl=en&lr=&safe=off&start=20&sa=N Visited = 05.06.05 20:44
WWW: URL=http://www.google.com Visited = 05.06.05 21:05
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095219,00.html Visited = 05.06.05 19:49
WWW: URL=http://images.google.com/images?q=cool+people&hl=en Visited = 05.06.05 20:41
WWW: URL=javascript:showTb(6595998,1); Visited = 05.06.05 21:25
WWW: URL=http://groups-beta.google.com/group/misc.jobs.resumes/msg/d607f8e1f396>98c7?dmode=source&hl=en Visited = 05.06.05 08:53
WWW: URL=http://www.sierra.ro/despre/img/FlugTag%20Aspach/06-FlugTag%20Aspach.jpg Visited = 05.06.05 20:42
WWW: URL=http://www.virustotal.com/flash/respuesta_sav/resultado?cfa1929f82049b3e1ba23bc66e91a84d:eng Visited = 05.06.05 11:51
WWW: URL=http://www.cinagen.com/aboutus.shtml Visited = 05.06.05 21:04
WWW: URL=http://www.aradcomm.co.il/content/archive_new.asp?ID=1369 Visited = 05.06.05 19:37
WWW: URL=http://laptop.shopy.co.il/products/24375 Visited = 06.06.05 00:00
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095189,00.html Visited = 05.06.05 18:19
WWW: URL=http://www.virustotal.com Visited = 06.06.05 09:27
WWW: URL=http://localhost:4664/redir?url=D%3A%5CDocuments+and+Settings%5CZak%5CDesktop%5Ccontacts%5C%D7%90%D7%99%D7%A6%D7%99%D7%A7+%D7%A4%D7%A7%D7%99%D7%9F%2Emsg&src=1&schema=8&start=1&s=Xruo--Pu4DEF9OW4rWdvbqtx9HU Visited = 05.06.05 20:22
WWW: URL=http://www.cnn.com/virtual/editions/europe/2000/roof/change.pop/frameset.exclude.html Visited = 06.06.05 10:37
WWW: URL=http://www.virustotal.com/flash/news Visited = 05.06.05 11:53
WWW: URL=https://secure.xeran.com/secure/login.bml?err= Visited = 05.06.05 10:03
WWW: URL=http://www.cinagen.com/detpages/aboutus7728.shtml Visited = 05.06.05 21:04
WWW: URL=http://www.google.com/search?hl=en&q=sl+500 Visited = 05.06.05 20:59
WWW: URL=http://www.google.com/search?hl=en&q=presentation Visited = 05.06.05 18:28
WWW: URL=http://www.google.com/search?hl=en&lr=&safe=off&q=%22donald+maycott%22 Visited = 05.06.05 21:05
WWW: URL=javascript:showTb(6595935,0); Visited = 05.06.05 21:25
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095031,00.html Visited = 05.06.05 23:55
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3094986,00.html Visited = 05.06.05 19:50
WWW: URL=http://images.google.com/imgres?imgurl=http://www.dannywhitfield.com/images/ITEM_13-B-2_MERCEDES_BENZ_SL-500_ROADSTER_RED_copy.jpg&imgrefurl=http://www.dannywhitfield.com/exotic.html&h=400&w=480&sz=200&tbnid=bemwgeRyNLwJ:&tbnh=105&tbnw=126&hl=en&start=2&prev=/images%3Fq%3Dsl%2B500%26hl%3Den%26lr%3D%26safe%3Doff%26sa%3DN Visited = 05.06.05 20:59
WWW: URL=http://www.xeran.com/webControl/emailpack/index.bml?tool=addresses Visited = 05.06.05 10:04
WWW: URL=http://desktop.google.com/plugins.html Visited = 05.06.05 09:33
WWW: URL=http://pbid.pro-market.net/engine?site=327+page=$188$+space=1884+link=$41911-34617-0-0=0$+goto=$http://www.interactika.co.il/clients/technion/toar2/default.asp?src=ynet268X195$ Visited = 06.06.05 00:15
WWW: URL=http://www.virustotal.com/flash/virustotal_en.html Visited = 05.06.05 11:49
WWW: URL=javascript:showTb(6595935,1); Visited = 05.06.05 21:25
WWW: URL=http://localhost:4664/redir?url=http%3A%2F%2Flocalhost%3A4664%2Fcache%3Fevent%5Fid%3D3645%26schema%5Fid%3D1%26q%3Dhissoft%26s%3DKNlhovhuil6rU%5Fqg8kGrqowI4nw&src=1&schema=1&start=1&s=4prVc1WSw94LPK8tt8A4A45o7k8 Visited = 05.06.05 20:31
WWW: URL=http://www.dannywhitfield.com/images/ITEM_13-B-2_MERCEDES_BENZ_SL-500_ROADSTER_RED_copy.jpg Visited = 05.06.05 20:59
WWW: URL=http://desktop.google.com/en/GoogleDesktopSearchSetup.exe Visited = 05.06.05 09:33
WWW: URL=http://www.dvtel.com Visited = 05.06.05 10:21
WWW: URL=http://web.utk.edu/~dolislag/miamidaddy.jpg Visited = 05.06.05 20:41
WWW: URL=http://groups-beta.google.com/group/misc.jobs.resumes/msg/d607f8e1f39698c7?dmode=source&hl=en Visited = 05.06.05 08:53
WWW: URL=http://www.debka.co.il/article.php?aid=1223 Visited = 05.06.05 21:28
WWW: URL=javascript:showTb(6595998,0); Visited = 05.06.05 21:26
WWW: URL=http://www.xeran.com/member Visited = 05.06.05 10:04
WWW: URL=javascript:showTb(6589845,1); Visited = 05.06.05 19:50
WWW: URL=http://localhost:4664/cache?event_id=3645&schema_id=1&q=hissoft&s=KNlhovhuil6rU_qg8kGrqowI4nw Visited = 05.06.05 20:31
WWW: URL=http://www.cinagen.com/pages/virtualdemos.shtml Visited = 05.06.05 21:05
WWW: URL=http://www.emediawire.com/releases/2004/5/emw128131.htm Visited = 05.06.05 21:05
WWW: URL=http://www.cnn.com Visited = 05.06.05 10:08
WWW: URL=http://www.omnivee.com/OVMovie.zip Visited = 05.06.05 11:34
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095245,00.html Visited = 05.06.05 21:24
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095272,00.html Visited = 06.06.05 00:15
WWW: URL=http://www.google.com/search?hl=en&lr=&safe=off&q=%22donald+maycott%22+cinagen Visited = 05.06.05 21:05
WWW: URL=http://www.secureol.com/team.htm Visited = 05.06.05 09:14
WWW: URL=http://www.google.com/search?hl=en&q=virustotal Visited = 05.06.05 11:49
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095203,00.html Visited = 05.06.05 21:24
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095026,00.html Visited = 05.06.05 19:20
WWW: URL=javascript:myopen('/webControl/emailpack/MailBoxesAdvanced.bml?show_access_info=1&popbox=ve2transfer@secureol.xeran.com','create','toolbar=no,location=no,directories=no,status=no,menubar=no,scrollbars=yes,resizable=yes,%20copyhistory=no,width=600,height=400,screenX=0,screenY=0,top=45,left=45') Visited = 05.06.05 10:05
WWW: URL=http://localhost:4664/search&s=wXUQk7tmzGpD8OvlGRKvBgpZOzk?q=hissoft&ie=UTF-8 Visited = 05.06.05 20:31
WWW: URL=http://www.secureol.com/cpanel Visited = 05.06.05 10:03
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3094960,00.html Visited = 05.06.05 18:19
WWW: URL=http://www.google.com/search?hl=en&safe=off&q=euro+integration&spell=1 Visited = 05.06.05 19:30
WWW: URL=http://www.txrollergirls.com/scrapbook/txrg82704_7/larrystern/Texas%20Rollergirls/slides/speedy%20and%20mel%20wanna%20make%20a%20sandwhich.JPG Visited = 05.06.05 20:44
WWW: URL=javascript:showTb(6596394,0); Visited = 05.06.05 21:27
WWW: URL=http://www.virustotal.com/flash/respuesta_sav/resultado?d61a6b3481b223ca66de8052560354dd:eng Visited = 06.06.05 09:30
WWW: URL=http://www.virustotal.com/flash/index_en.html Visited = 06.06.05 09:28
WWW: URL=http://www.ynet.co.il/home/0,7340,L-8,00.html Visited = 06.06.05 11:35
WWW: URL=http://www.linkinformationsystems.com/aboutus.php Visited = 05.06.05 09:15
WWW: URL=http://members.xeran.com/webControl/emailpack/MailBoxesAdvanced.bml?show_access_info=1&popbox=ve2transfer@secureol.xeran.com Visited = 05.06.05 10:05
WWW: URL=javascript:showTb(6589845,0); Visited = 05.06.05 19:51
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095100,00.html Visited = 05.06.05 23:55
WWW: URL=http://www.linkinformationsystems.com/members.php Visited = 05.06.05 09:14
WWW: URL=http://www.pcmag.com/article2/0,1759,1777825,00.asp Visited = 06.06.05 00:02
WWW: URL=http://members.xeran.com/webControl/emailpack/MailBoxesAdvanced.bml Visited = 05.06.05 09:05
WWW: URL=http://images.google.com/images?hl=en&lr=&safe=off&q=flugtag Visited = 05.06.05 20:41
WWW: URL=http://www.secureol.com/team.html Visited = 05.06.05 09:14
WWW: URL=http://images.google.com/imgres?imgurl=http://web.utk.edu/~dolislag/miamidaddy.jpg&imgrefurl=http://web.utk.edu/~dolislag/coolpeoplepage.html&h=534&w=360&sz=31&tbnid=wqyuqM9Dle8J:&tbnh=129&tbnw=86&hl=en&start=1&prev=/images%3Fq%3Dcool%2Bpeople%26hl%3Den%26lr%3D%26safe%3Doff Visited = 05.06.05 20:41
WWW: URL=http://192.168.1.1 Visited = 05.06.05 12:18
WWW: URL=http://desktop.google.com/?promo=mp-gds-v1-1 Visited = 05.06.05 09:32
WWW: URL=http://images.google.com/images?hl=en&lr=&safe=off&q=psycho+people Visited = 05.06.05 20:42
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095186,00.html Visited = 05.06.05 23:55
WWW: URL=http://www.google.com/search?hl=en&lr=&safe=off&q=dechovich Visited = 05.06.05 09:08
WWW: URL=res://D:\WINDOWS\system32\shdoclc.dll/navcancl.htm Visited = 06.06.05 11:35
WWW: URL=http://www.virustotal.com/flash/envio_sav_anonimo Visited = 06.06.05 09:28
WWW: URL=http://www.cinagen.com/extra2.shtml Visited = 05.06.05 17:57
WWW: URL=http://localhost:4664/search&s=wXUQk7tmzGpD8OvlGRKvBgpZOzk?q=%D7%99%D7%95%D7%A1%D7%99+%D7%A4%D7%A7%D7%99%D7%9F Visited = 05.06.05 20:22
WWW: URL=http://www.virustotal.com/flash/respuesta_sav/resultado?552fb14b20bb65b4d0e171f013053ce6:eng Visited = 05.06.05 11:53
WWW: URL=http://home.arcor.de/benjamin_mueller/modellfluggruppe/jpg/galerie/ft2000/flugtag-2000-k9.jpg Visited = 05.06.05 20:42
WWW: URL=http://images.google.com/images?q=crazy+people&hl=en&lr=&safe=off&start=20&sa=N Visited = 05.06.05 20:43
WWW: URL=javascript:showTb(6596394,1); Visited = 05.06.05 21:26
WWW: URL=https://secure.xeran.com/secureLogin Visited = 05.06.05 10:04
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095168,00.html Visited = 05.06.05 19:49
WWW: URL=http://localhost:4664/search&s=wXUQk7tmzGpD8OvlGRKvBgpZOzk?q=his+soft Visited = 05.06.05 20:31
WWW: URL=http://www.linkinformationsystems.com Visited = 05.06.05 09:13
WWW: URL=http://www.dvtel.com/company_mt.asp Visited = 05.06.05 10:22
WWW: URL=http://www.cinagen.com/detpages/aboutus7727.shtml Visited = 05.06.05 17:57
WWW: URL=http://www.google.com/search?hl=en&q=donald+mycott Visited = 05.06.05 21:05
WWW: URL=http://www.linkinformationsystems.com/news.php Visited = 05.06.05 09:15
WWW: URL=http://www.cinagen.com Visited = 05.06.05 21:04
WWW: URL=http://www.google.com/search?hl=en&q=euro+integrator Visited = 05.06.05 19:30
WWW: URL=http://web.utk.edu/~dolislag/farmbook.html Visited = 05.06.05 20:41
WWW: URL=http://www.debka.co.il Visited = 06.06.05 11:35
WWW: URL=http://www.cinagen.com/detpages/aboutus7725.shtml Visited = 05.06.05 17:57
WWW: URL=http://www.edm.luc.ac.be/uixml2004/presentations/Abrams-WDUIXML_rev04-FINAL.ppt Visited = 05.06.05 18:28
WWW: URL=http://www.bleedingsnort.com/cgi-bin/viewcvs.cgi/Stable/VIRUS/TROJAN_Hotword?rev=1.1&view=auto Visited = 05.06.05 08:54
WWW: URL=http://images.google.com/images?hl=en&lr=&safe=off&q=wanna+be Visited = 05.06.05 20:44
WWW: URL=http://www.dvtel.com/newsupdates.asp Visited = 05.06.05 10:22
WWW: URL=http://www.google.com/imghp?hl=en&tab=wi&q= Visited = 05.06.05 20:41
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3094948,00.html Visited = 06.06.05 00:03
WWW: URL=http://www.google.com/intl/en/options Visited = 05.06.05 09:32
WWW: URL=http://desktop.google.com/developer.html Visited = 05.06.05 09:33
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095049,00.html Visited = 05.06.05 19:17
WWW: URL=http://www.google.com/search?hl=en&lr=&safe=off&q=secureol+ Visited = 05.06.05 09:08
WWW: URL=http://www.acronis.com Visited = 05.06.05 18:22
WWW: URL=file:///D:/Documents%20and%20Settings/Zak/Desktop/IL-trojan.txt Visited = 06.06.05 11:35
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095206,00.html Visited = 05.06.05 20:14
WWW: URL=http://images.google.com/images?hl=en&lr=&safe=off&q=crazy+people Visited = 05.06.05 20:43
WWW: URL=http://www.cinagen.com/detpages/aboutus7726.shtml Visited = 05.06.05 17:57
WWW: URL=http://www.acronis.com/enterprise/products/ATIESWin Visited = 05.06.05 18:22
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095162,00.html Visited = 05.06.05 19:17
WWW: URL=http://images.google.com/images?q=sl%20500&hl=en&lr=&safe=off&sa=N&tab=wi Visited = 05.06.05 20:59
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3095138,00.html Visited = 05.06.05 18:18
WWW: URL=http://www.ynet.co.il/articles/0,7340,L-3094968,00.html Visited = 05.06.05 18:19
WWW: URL=http://www.google.com/search?hl=en&lr=&safe=off&q=presentation+ppt Visited = 05.06.05 18:28
WWW: URL=http://localhost:4664/search&s=wXUQk7tmzGpD8OvlGRKvBgpZOzk?q=%D7%A4%D7%A7%D7%99%D7%9F&ie=UTF-8 Visited = 05.06.05 20:22
WWW: URL=http://www.mdcbowen.org/cobb/archives/comic/20031210-377-GirlsJust-thumb.jpg Visited = 05.06.05 20:44
WWW: URL=about:blank Visited = 05.06.05 23:50
WWW: URL=http://www.ynet.co.il Visited = 06.06.05 11:35
WWW: URL=http://www.linkinformationsystems.com/contactus.php Visited = 05.06.05 09:15
WWW: URL=http://www.google.com/search?hl=en&q=%22%D7%90%D7%9C%D7%99+%D7%90%D7%97%D7%99+%D7%9E%D7%A8%D7%93%D7%9B%D7%99%22 Visited = 05.06.05 19:37
WWW: URL=http://members.xeran.com/webControl/emailpack/index.bml?tool=addresses Visited = 05.06.05 10:04
©2000-2015 Target Eye LTD (UK)
All materials contained on this article are protected by International copyright law and may not be used, reproduced, distributed, transmitted, displayed, published or broadcast without the prior written permission given by Target Eye LTD (UK). You may not alter or remove any trademark, copyright or other notice from copies of the content.



No comments:
Post a Comment